Think Linux is Virus-Proof? Think Again. We Battled a Sophisticated Attack and Won.
We recently battled a sophisticated cryptojacking and botnet attack on one of our production servers. Our analysis suggests the attackers were Diicot, an emerging Romanian threat actor. They attempted to use a combination of a crypto miner and a DarkNexus Trojan to steal resources and potentially launch DDoS attacks or exfiltrate data.
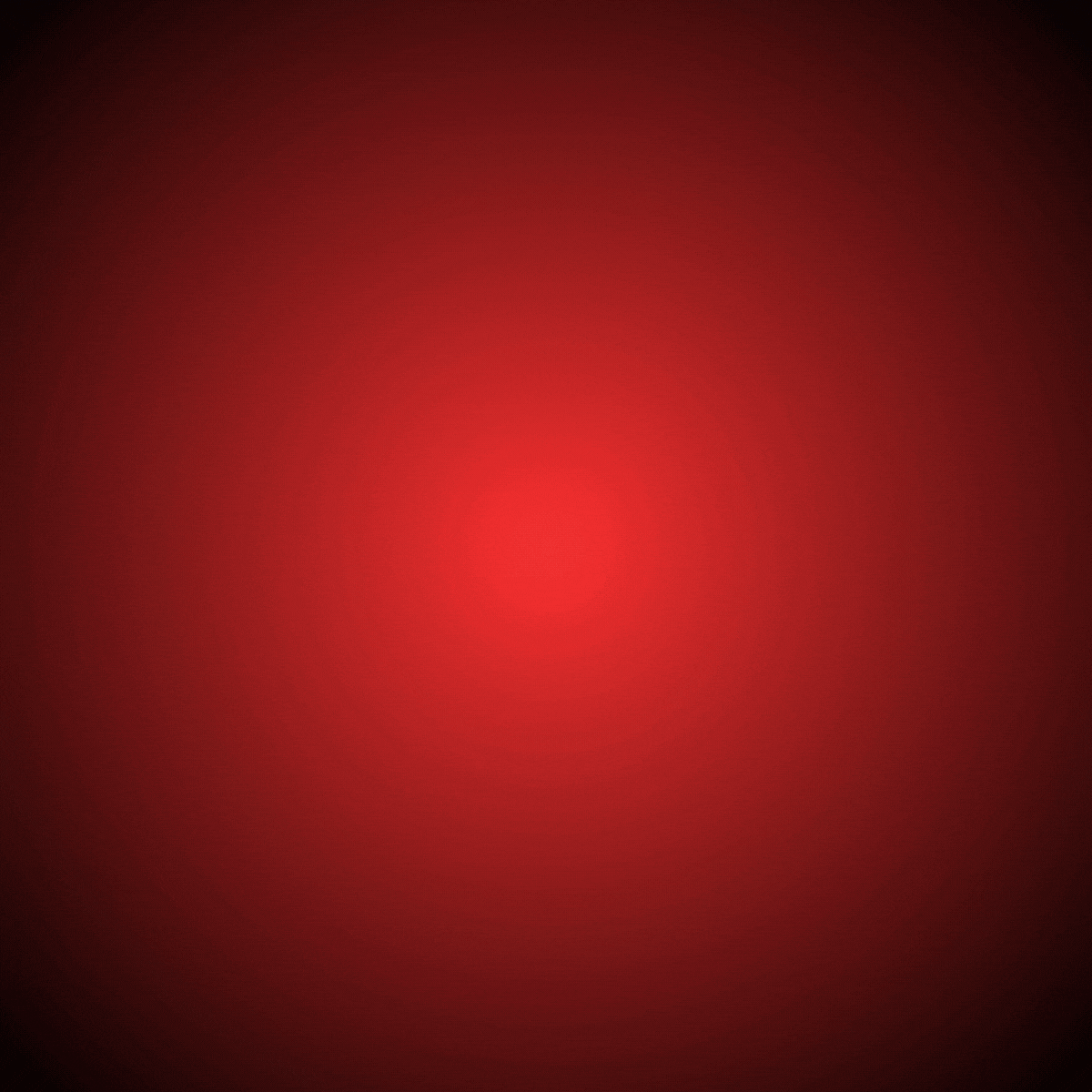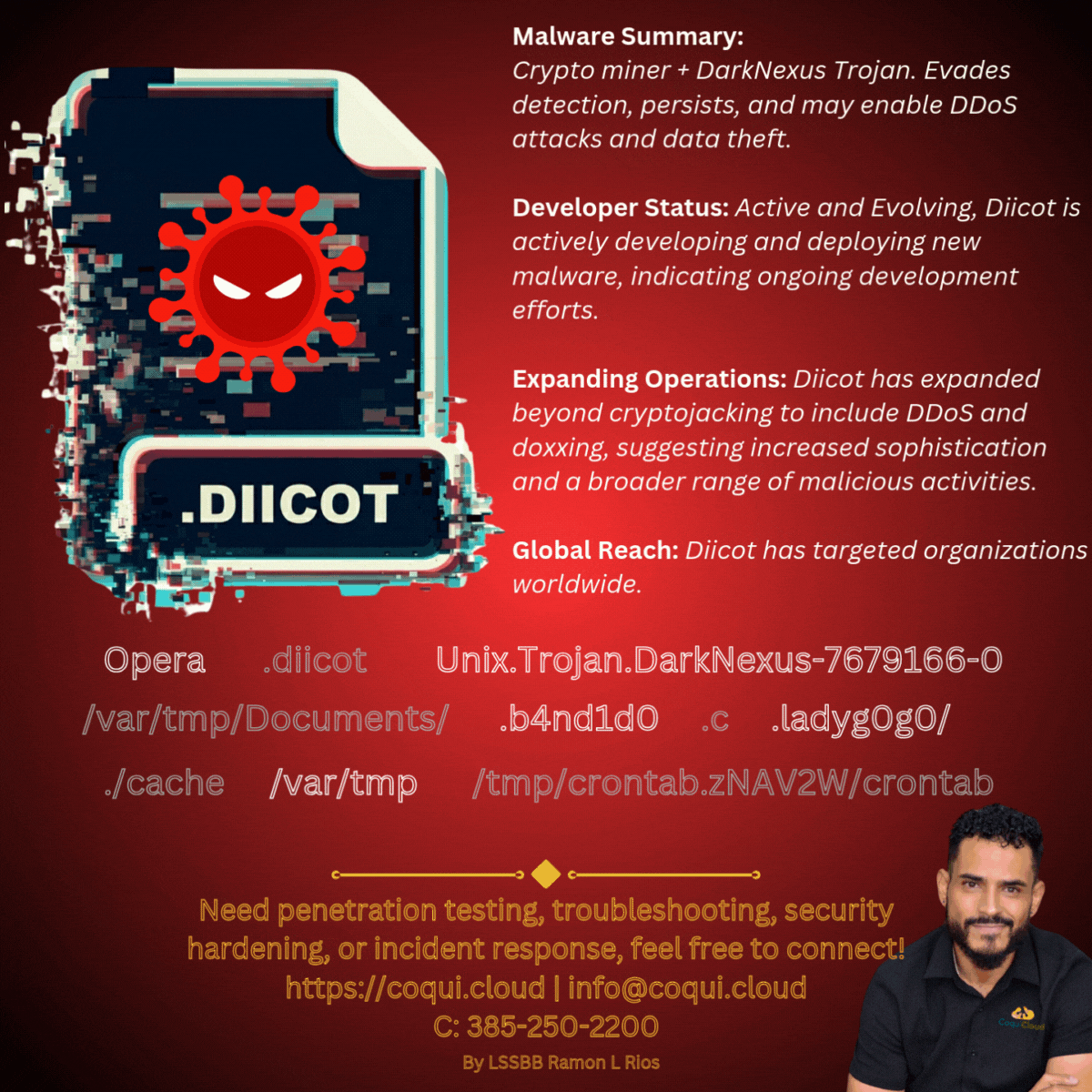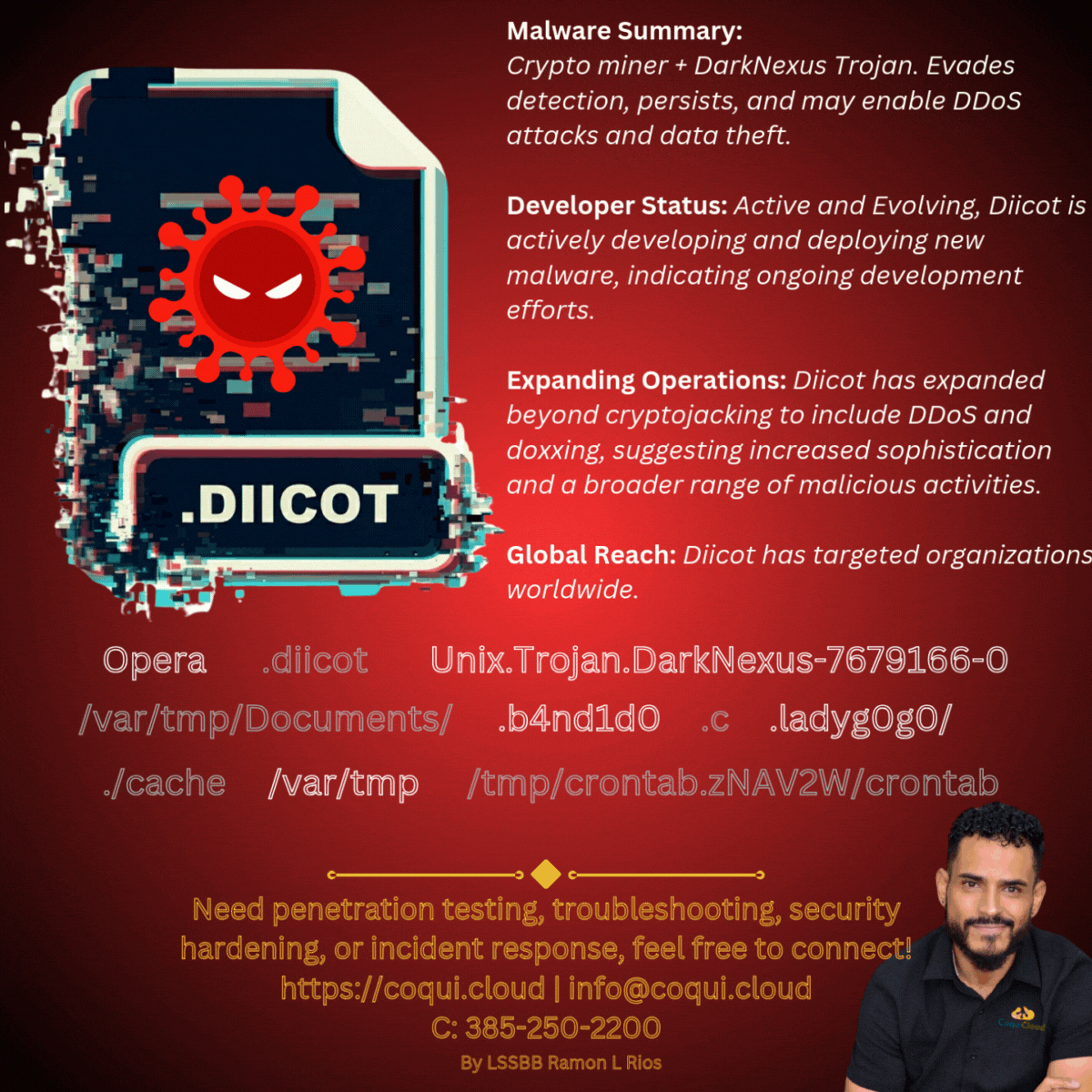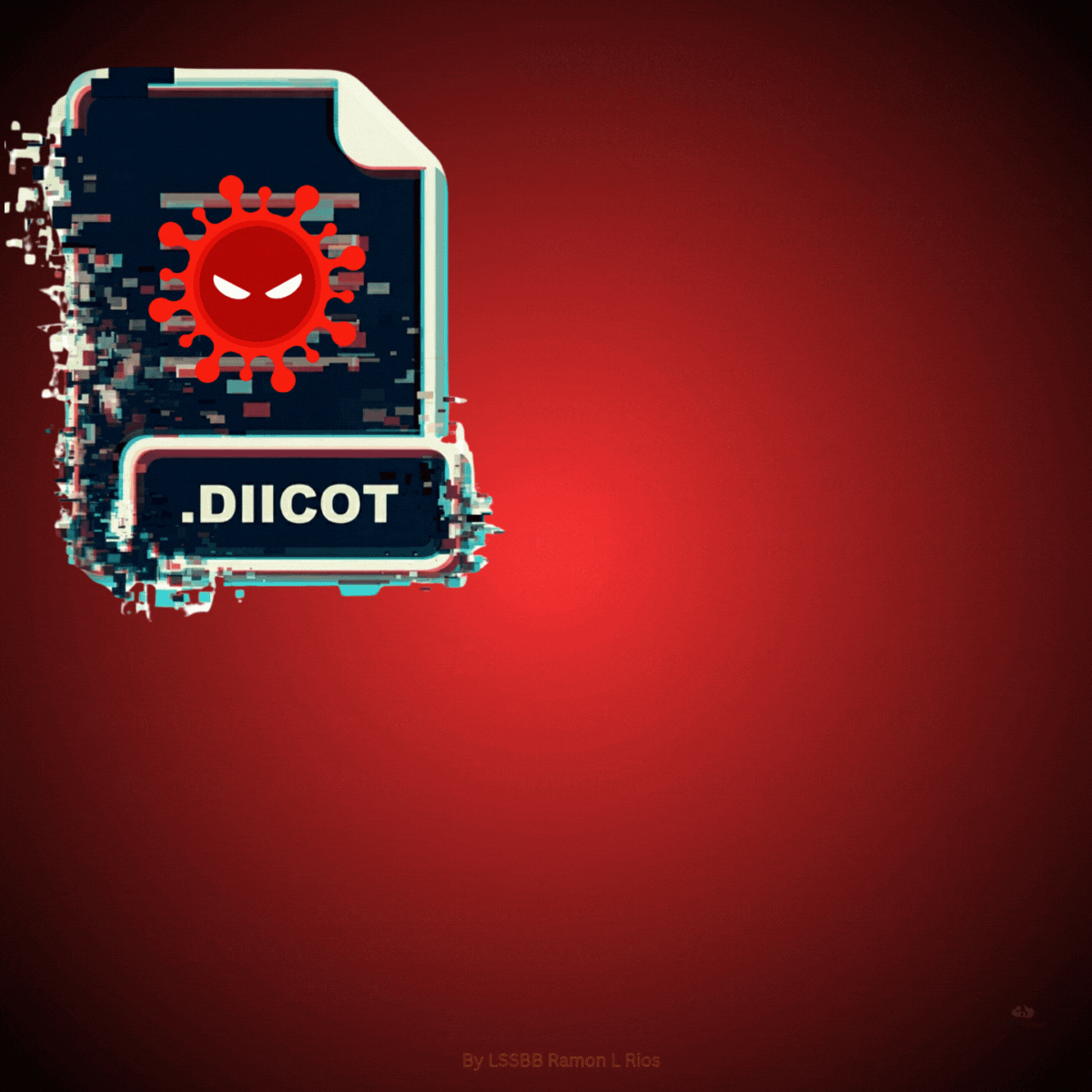
This was a challenging incident. The malware was designed to evade detection, with obfuscated code and hidden persistence mechanisms. It even created new files and directories with deceptive names to blend in with the system.
Our response involved:
- Malware analysis: We analyzed malicious files using various tools and techniques to understand their behavior and purpose.
- Threat hunting: We actively searched for and identified hidden malware components and persistence mechanisms.
- Incident response: We removed the malware, terminated malicious processes, and cleared cron jobs that were re-spawning the threats.
- Security hardening: We implemented security measures like firewall configuration, user permission reviews, and software updates to prevent future attacks.
This incident highlights why we take security seriously at Coqui Cloud and the importance of:
- Proactive threat hunting: Regularly searching for signs of compromise, even when no alarms are triggered.
- Defense in depth: Implementing multiple layers of security to protect against various attack vectors.
- Continuous monitoring: Constantly monitoring systems and logs for suspicious activity.
If you're looking for help with penetration testing, troubleshooting, security hardening, or incident response, feel free to connect! We're always open to discussing how we can help organizations improve their security posture.

Think Linux is Virus-Proof? Think Again. We Battled a Sophisticated Attack and Won.